Transport for London TfL Data Harvesting.
Syndication Developer Guidelines Transport for London Data Service
The dangers of data harvesting
“A common technique involves deploying bots to collect user information—including contact details, personal data, and payment information—often without the user’s awareness. This bot-powered harvesting is also known as data scraping.
Essentially, data harvesting is a method for gaining insights into specific individuals, consumer groups, and even the larger public. Businesses, for instance, engage in this form of data collection to display relevant ads to their users.”
https://www.humansecurity.com/learn/topics/what-is-data-harvesting/
“Scraping; Web scraping, or content scraping, is the practice of using automated bots and web crawlers to extract content or data from third-party websites. The scraper can then replicate this data on another website or application.”
https://www.humansecurity.com/learn/topics/what-is-scraping/
Syndication Developer Guidelines Transport for London Data Service Version 2.0 (2012-05-21)
“Our aspiration is to publish TfL data in a format which maximises its accessibility and usefulness to developer partners, wherever legally, commercially and technically possible.”
https://tfl.gov.uk/cdn/static/cms/documents/syndication-developer-guidelines.pdf
Since when is the data of Commuters in London scanned and surveyed 24/7 in every road crossing, tube station, and streets allowed to be sold to Corporates usually as money making advertising targeting?
If they do it for the Transport for London TfL then they also do it for data collected from all Traffic Management Systems in all Local Authorities in the UK.
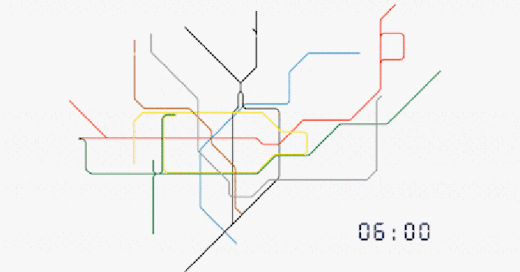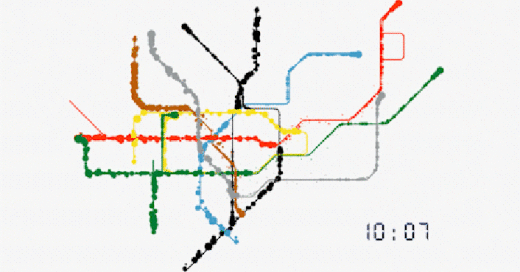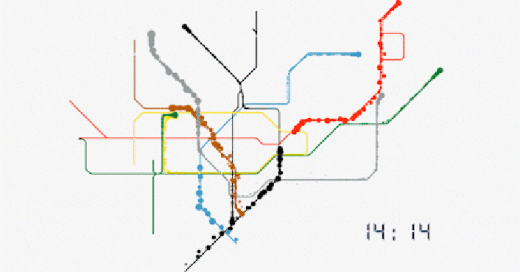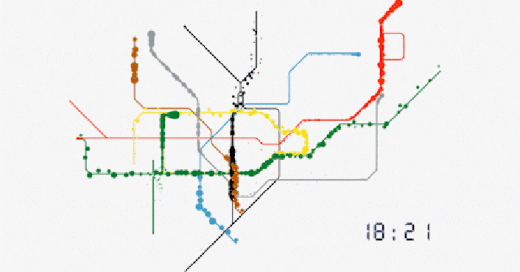
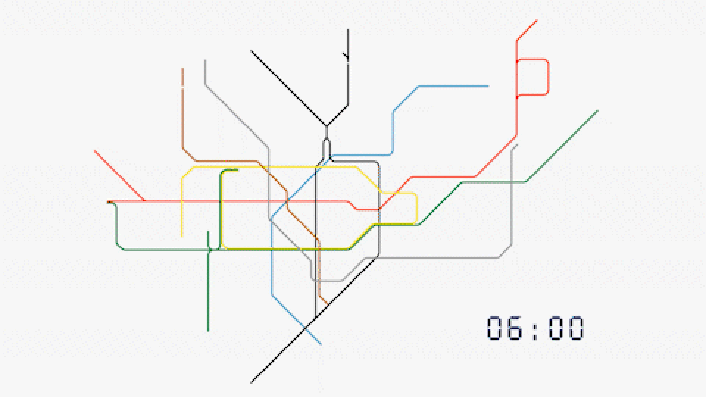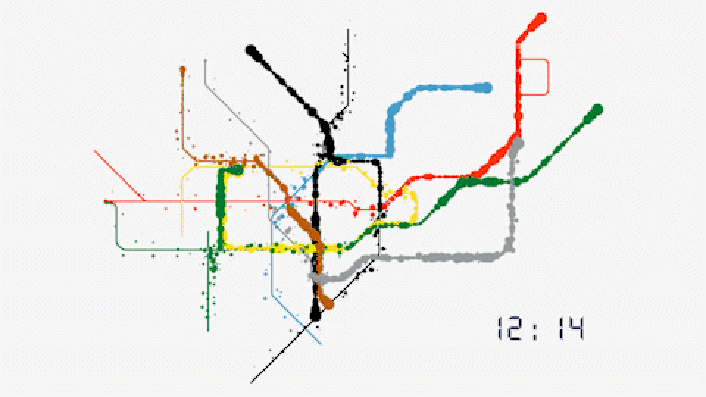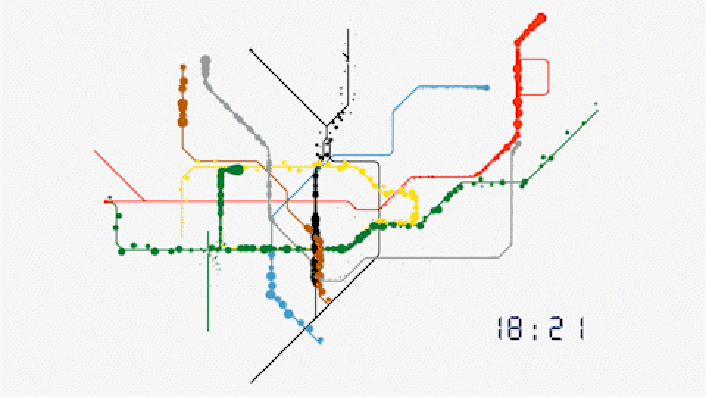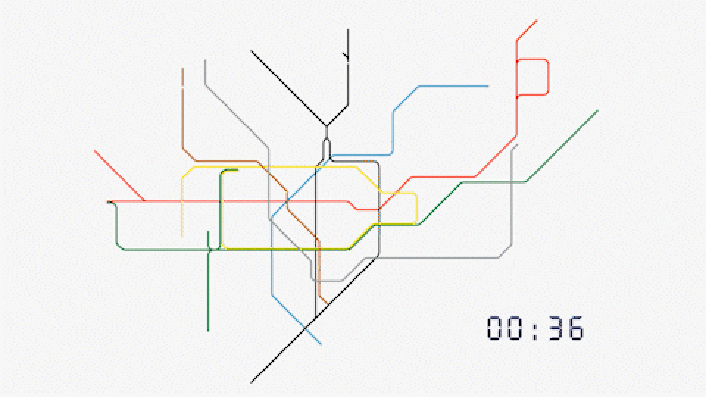
No. This is not a schematic for the movement of Nano Lipids in the blood, but real time Data Harvesting analysis of passenger movements in Transport for London TfL tube stations.
Almost certainly the same issues apply to their Ulez schemes and Smart Traffic Management data collection to be recycled for sale to any TfL Syndicated Developer.
Supposedly anonymised as personal data available to be used for their profit making schemes such as Advertising.
Who decided that TfL can supply Syndicated Developers our unconsented access to our data, movement, and location?
TfL; Evolution of our data
”In the last week, 50% of journeys made on the Tube involved at least one interchange. Our offering allows clients to target audiences more efficiently throughout the course of their journey.
It offers real reach, real frequency.
For any combination of frames, corridors, platforms or stations, we can identify the unique number of people that have been in those areas. We can also identify the number of times they have been there. No other environment in the world has this capability. Our data on real people in the real world is sourced directly from our data.”
https://madeby.tfl.gov.uk/2022/04/28/evolution-data/
also
https://i0.wp.com/madeby.tfl.gov.uk/wp-content/uploads/2022/04/Tube-map-customer-data-animation-London.gif?resize=706%2C397&ssl=1
That then begs the question what personalised data is being harvested from Smart Traffic management System as the use of Lidar-Laser, and 24Ghz Radar allows personal identification using Bluetooth, WiFi, Engine management codes, and Media Access Codes MAC presumably anyone with an artificial transplant pacemaker etc, barcodes emanating from lanthanide contamination if Jabbed (most vaccine adjuvants, and pseudo-magnetic lanthanides Cerium, Gadolinium used in PET and MRI scans to “light up” the individual).
TfL; Open data users
”All public TfL data (or 'open data') is freely released here for developers to use in their own software and services.”
https://tfl.gov.uk/info-for/open-data-users/
A long list of TfL data collection. Data update every 2 minutes.
”All public TfL data (or 'open data') is freely released here for developers to use in their own software and services.”
https://tfl.gov.uk/info-for/open-data-users/our-open-data?intcmp=3671#on-this-page-1
When Corporates use data harvesting to target their “commercial” products, has TfL allowed their Smart Traffic Managements Systems for that use?
Increasingly TfL’s Tube Underground data collections appears to be used with the same data harvesting at a personal level as happened with Facebook and Cambridge Analytics fiasco?
A supposed Fusion Smart Traffic Management Systems anonymised data collection that appears to be capable of unanonymised personal identification through your Mobile phone, Bluetooth, WiFi, or MAC address emanating from every person that is scanned by TfL scanning Lidar-radar24Ghz data systems.
TfL Syndicated Developer policy on who can access their data.
Syndication Developer Guidelines Transport for London Data Service Version 2.0 (2012-05-21)
“Our aspiration is to publish TfL data in a format which maximises its accessibility and usefulness to developer partners, wherever legally, commercially and technically
possible.”
https://tfl.gov.uk/cdn/static/cms/documents/syndication-developer-guidelines.pdf
If they do it for their London Underground Tube system then they also do it for data collected from Traffic Management Systems, however Smart Traffic Management system can identify the persons ID via multiple Lidar-laser, 24Ghz Radar, and Camera facial recognition, mobile phone ID, Engine Management ID, Bluetooth device, and Wifi laptops, as well as MAC “barcode” addresses emanating from implants, and capable of ID though blood stream toxins, any contamination due to medical interventions, and vaccine heavy metals-rare earth adjuvants.
Not only does Smart Traffic Management Systems irradiating-scanning EMF 24Ghz capable of data harvesting, but also evidenced research that it causes excitation of those blood stream toxins to be even more toxic.
Has TfL that brags about its Open data collated data harvesting also doing the same as Facebook-Cambridge Analytics in 2010 resulting in a debacle to monetarise people’s personal data and movements.
TfL do charge for the Open data services to those “syndicated developers”.
Facebook–Cambridge Analytica data scandal
”In the 2010s, personal data belonging to millions of Facebook users was collected by British consulting firm Cambridge Analytica for political advertising without informed consent.”
https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
Is TfL doing similar with unsuspecting London commuters?
Then consider those same Smart Traffic Management Systems are deployed in every UK Local Authority as also wide open to similar unconsented data harvesting abuse.
There are companies that are already interconnected with TfL and use of commuter data harvesting to inform unconsenting commuters for advertising targeting.
”Captcha” is not necessarily an algorithm to detect “Bots”.
As a Corporate, it too requires large amounts of data. In this case to identify humans from virtual electronics, but also on this issue as a subsidiary of Google as not particularly trustworthy.
Which then leads to the compounded issue of data collection and manipulated search engines to deliver their preferred products.
Not only multiple “Facebook-Cambridge Analytics” scenarios, but also the use of unconsented data harvesting using search engines especially Google.
All of which defines a society manipulated by BigTech, Social Media Platforms, Governments, and TfL, Local Authorities who use EMF irradiation surveillance, and invasive unconsented data harvesting to interfere, and deny our civil liberties.
An issue that requires an update on identified companies using TfL antics as Local Authorities supposed anonymised Fusion Smart traffic data for their own money making schemes usually advertising but also politics.
Government would have you believe
Using CAPTCHA
https://www.gov.uk/service-manual/technology/using-captchas
also as
Honeypot (computing)
“In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site which contains information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is similar to police sting operations, colloquially known as "baiting" a suspect.”
https://en.wikipedia.org/wiki/Honeypot_(computing)
CAPTCHA; Completely Automated Public Turing test to tell Computers and Humans Apart."
Simple? Not so, as it now uses huge databases through Data Harvesting to categorise aswell as site based interrogations of Websites.
reCaptcha is a Google Company
Is supposed anonymised data such as captcha really anonymous?
Look to the Facebook-Cambridge Analytics as to where data Harvesting is going.
Not just one company, and an issue that has not gone away with all Advertising Corporates, and Politicians looking to your personal data to predict individual behaviour, politics, and then to manipulate your outcomes for buying, voting, and travel.
What is reCAPTCHA?
Instead of showing a CAPTCHA challenge, reCAPTCHA v3 returns a score so you can choose the most appropriate action for your website.
https://developers.google.com/recaptcha/
Adaptable risk analysis engine assigns a risk score to each phone number, helping organizations to identify those at risk of involvement in SMS toll fraud attacks.
https://cloud.google.com/security/products/recaptcha
There is no anonymity in the world of BigTech.